What is Azure Identity Protection?
Microsoft Azure Identity Protection is a part of Microsofts Security Services and can be found in the Azure Portal and also nowadays in the Microsoft Entra Admin Center.
With Azure Identity Protection, Administrators can detect, analyze and remediate identity-based attacks on their users’ Azure Active Directory Accounts. Identity Protection uses machine learning to detect suspicious activities such as risky sign-ins from anonymous or known malware-linked IP addresses, unusual travel activities, compromised user credentials, and more. These risks can then be self-remediated by, for example, allowing user access only, if a successful multifactor authentication is done, the user made a password reset, or an administrator unlocks the user account after it has been blocked.
Examples of sign-in risks are atypical travel, malware-linked IP address, suspicious browser, malicious IP addresses, password spray, Anonymous IP addresses, or impossible travel.
Examples of user risks are anomalous user activity or leaked credentials.
How to configure Azure Identity Protection?
To enable Azure Identity Protection with self-remediation, you need to roll out the multifactor authentication first via the “Multifactor authentication registration policy“, which can also be found in the Identity Protection configuration pane. Otherwise, if a user cannot sign in, an administrator must manually approve the sign-in to allow the user to proceed with their work because self-remediation isn’t possible without multifactor authentication.
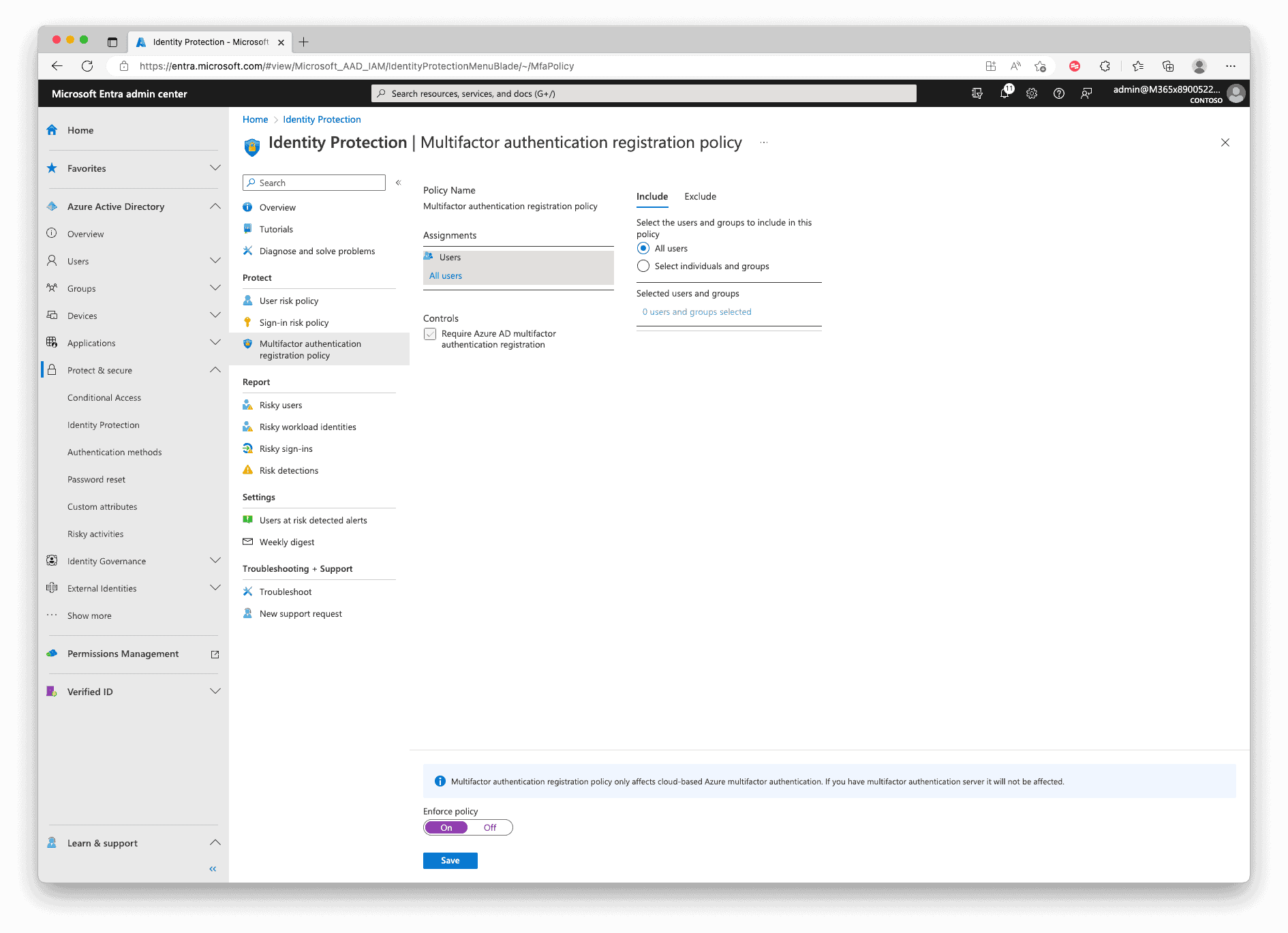
After the rollout, you can configure the risk policies by navigating to the Azure Portal, then “Azure Active Directory“, and selecting the “Security” menu. You can configure the “User risk policy” and “Sign-in risk policy” easily there.
But my new preferred way I will describe here is the configuration via the Microsoft Entra Portal and Conditional Access Policies, this will be the way to go in the near future. To reach Entra, you can navigate to https://entra.microsoft.com, in the menu on the left, search for “Azure Active Directory” and hit “Protect & Secure“.
Navigate to “Conditional Access” and click “Policies“. You can configure both the user and sign-in risk policy there, but get more control and options than the old configuration process. Here click “New Policy” to create a new policy.
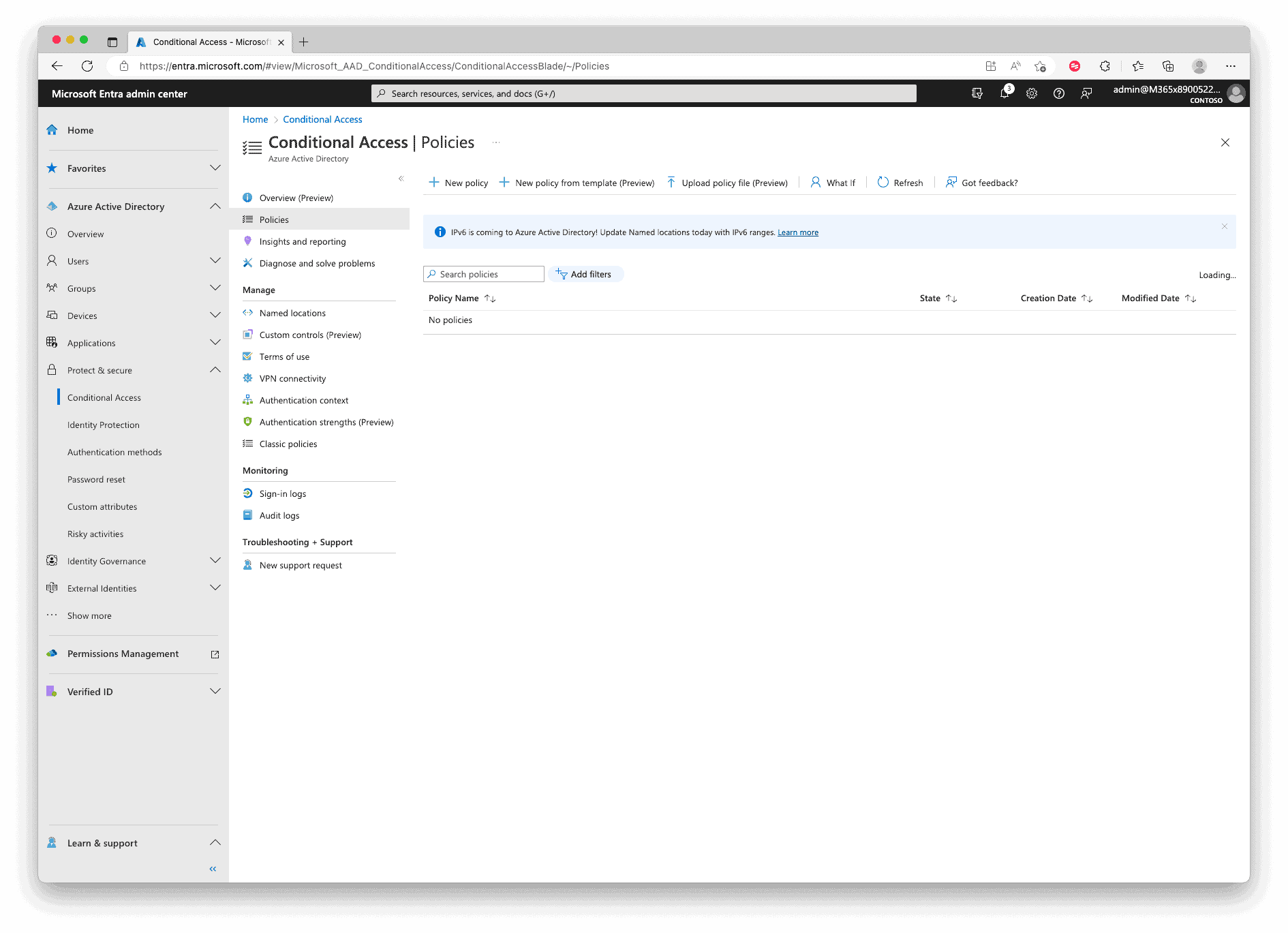
During the creation of the policy, under the “Users” settings include all users. Create exceptions for accounts like yours and other admin accounts, otherwise, you can easily lock out yourself.
Select “all Cloud Apps” in the scope for “Cloud apps or actions“, and for “Conditions“, activate and configure User risk with the Low, Medium, and High Levels. We will duplicate this Policy after the creation for the Sign-in Risk policy because we got different Grant options for self-remediation.
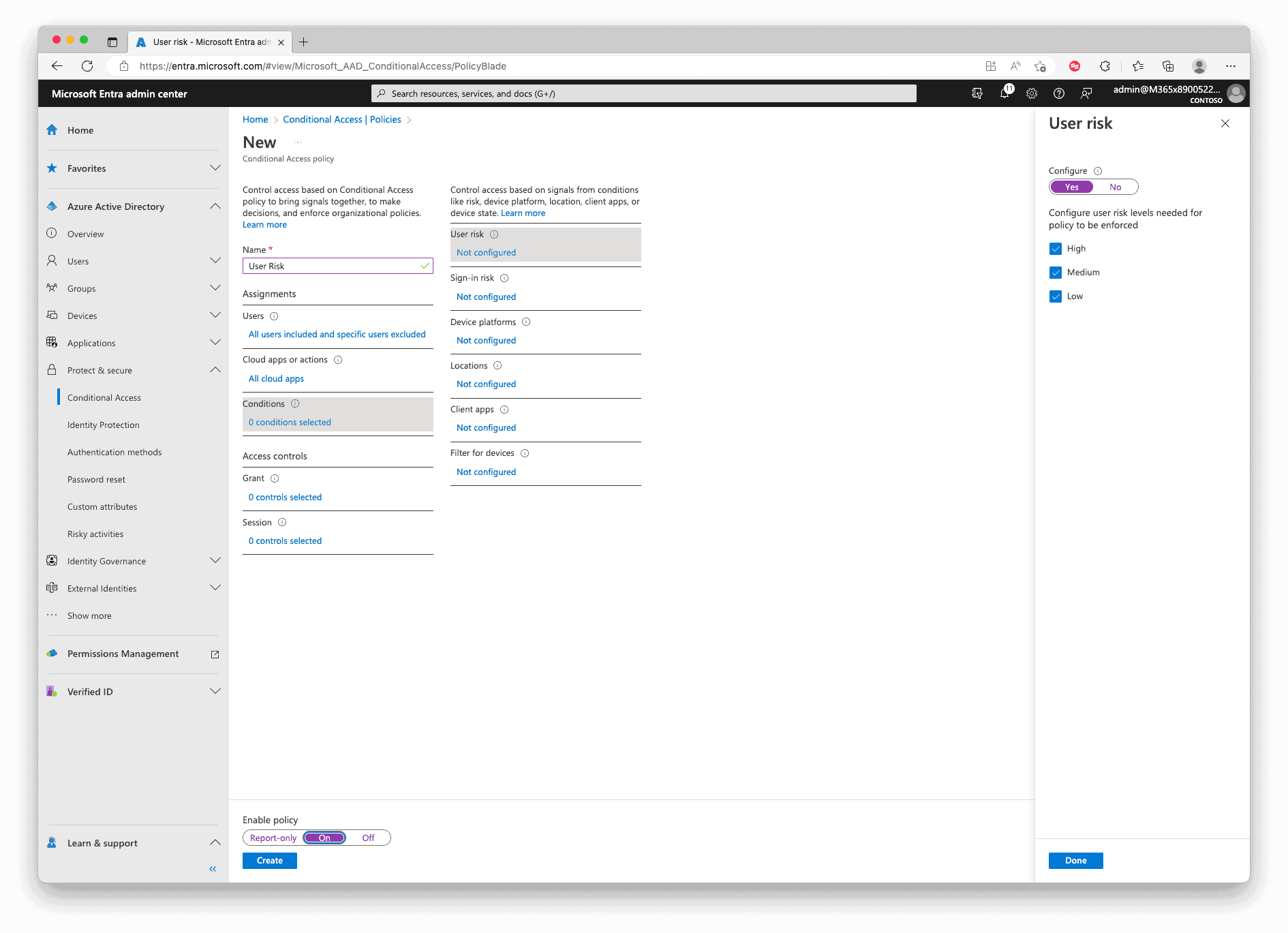
Now in the Grant section, select “Allow access“, check “Require multifactor authentication” and then “Require password change“. In the end, set the “Enable Policy” at the bottom to “On” and “Create” the policy.
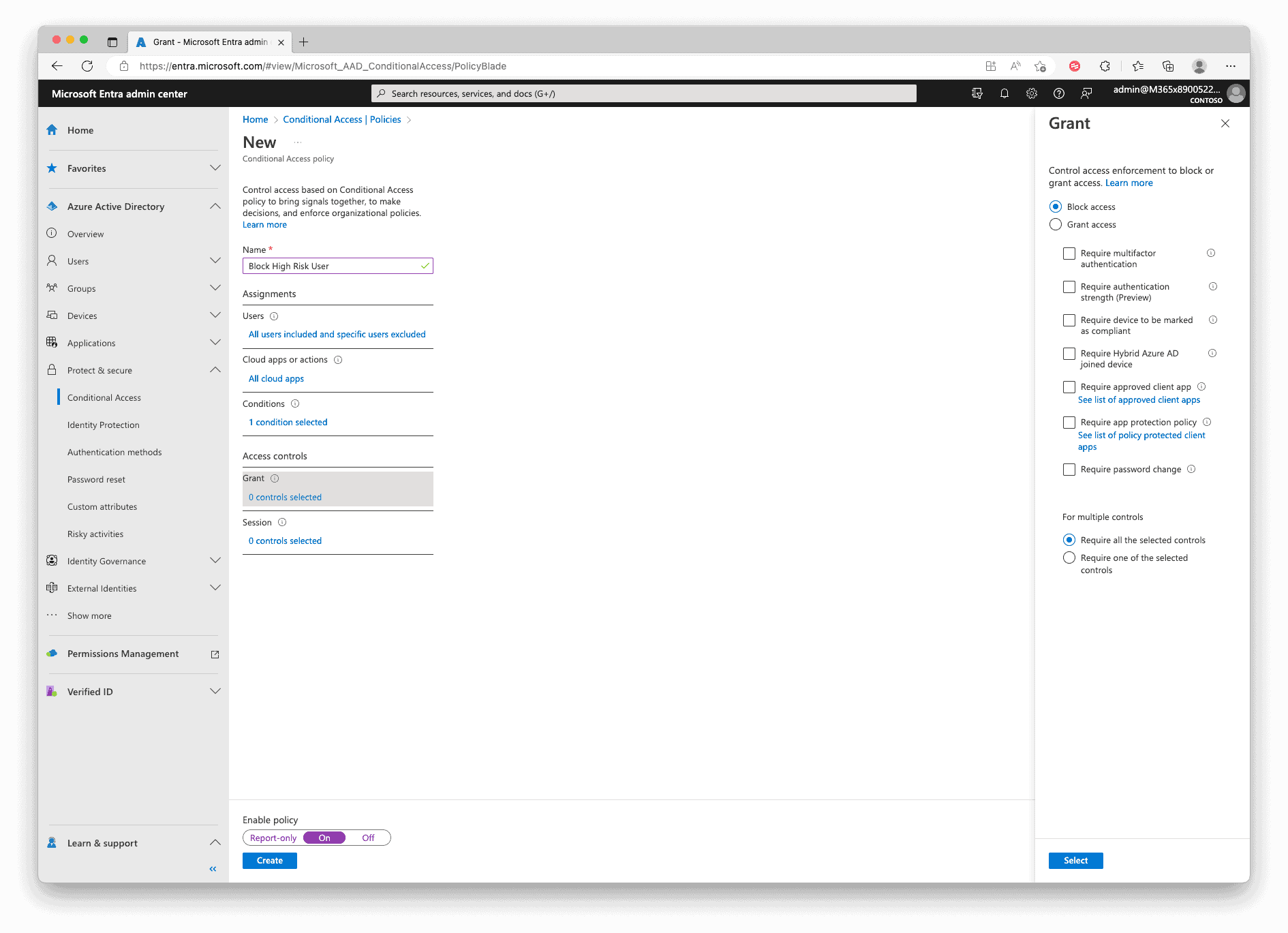
In the Policy Overview, duplicate the newly created Policy.
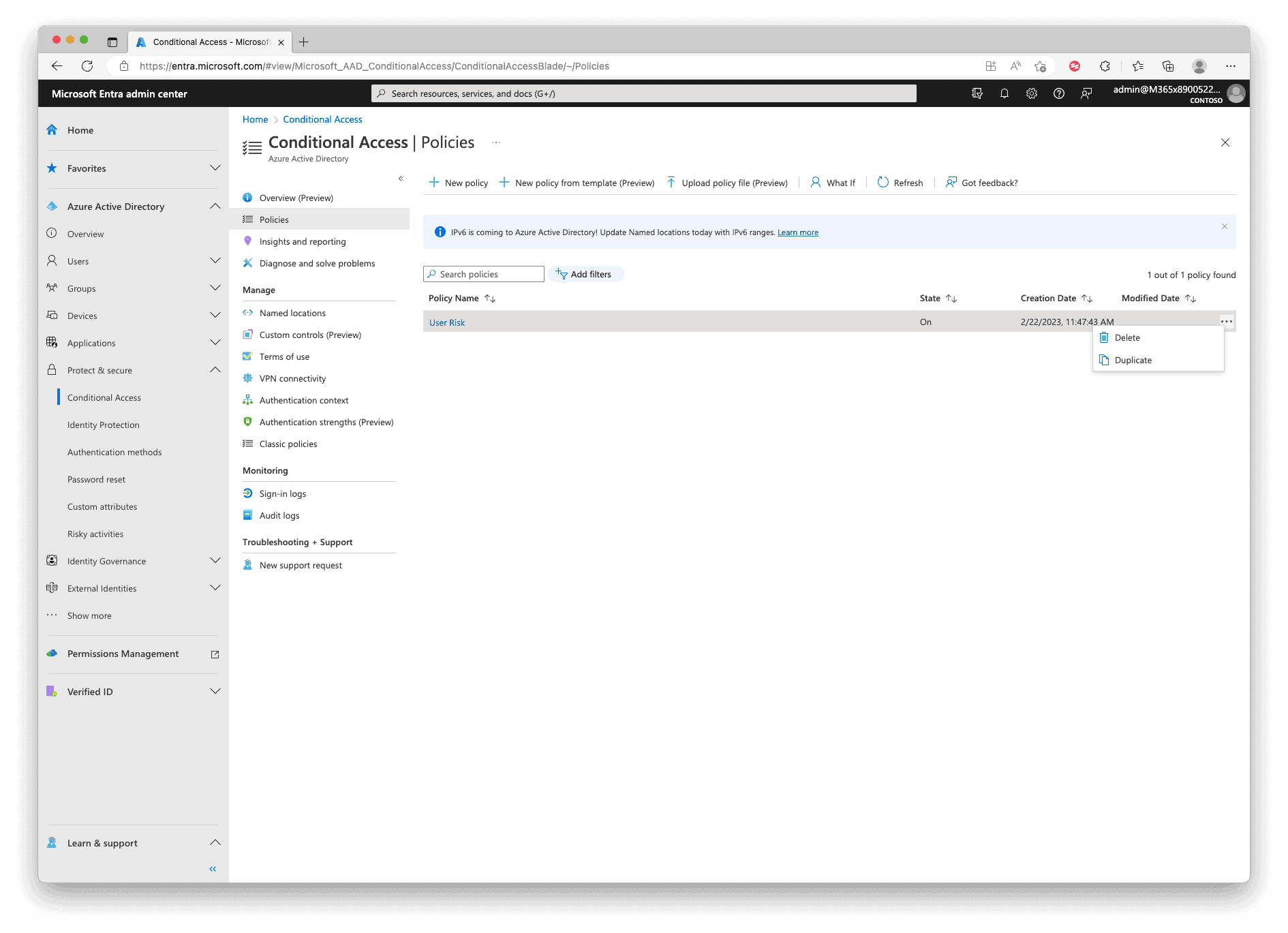
Change the Name, the Conditions to “Sign-in Risk“, check the Levels “Low, Medium and High”.
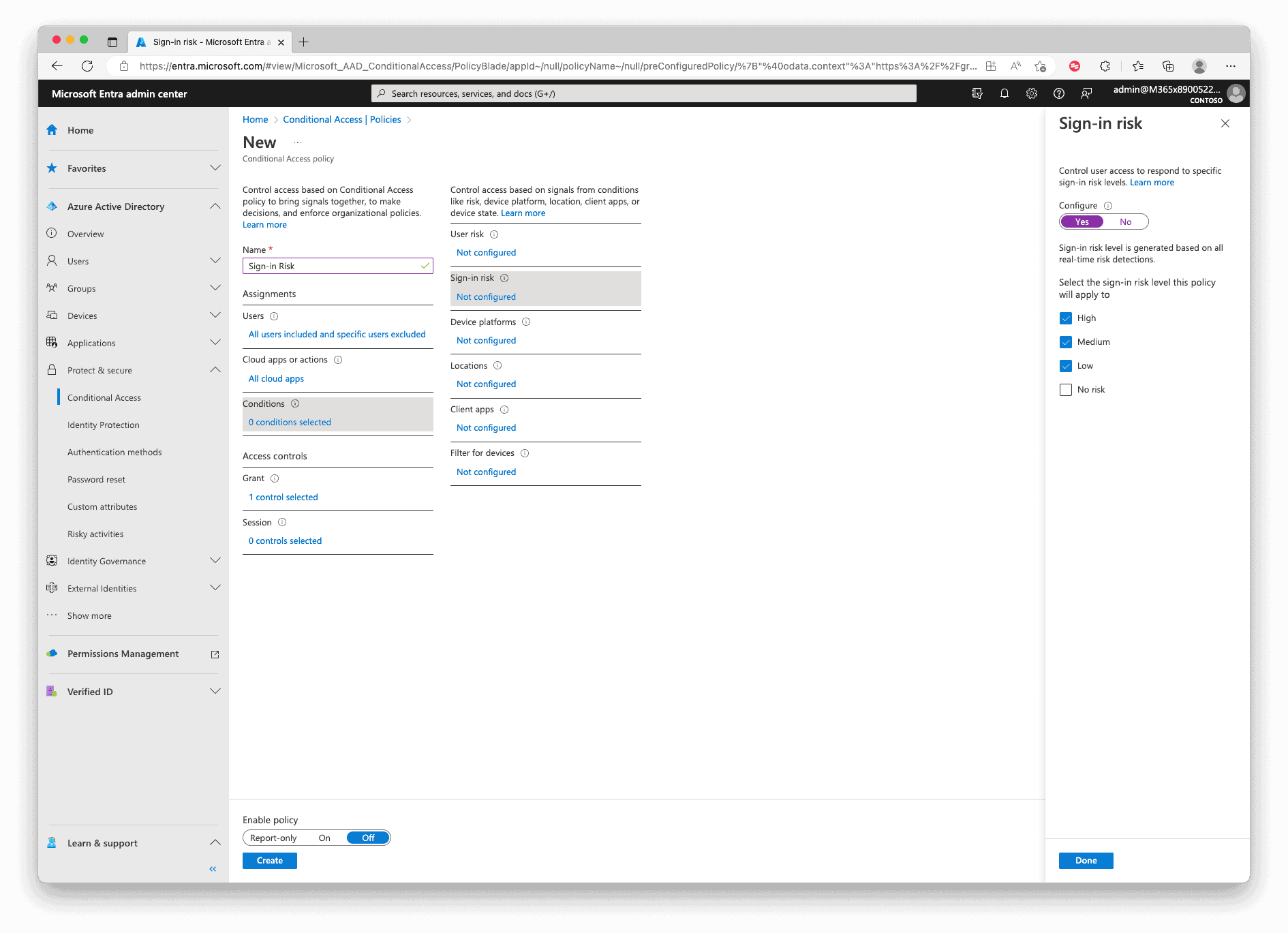
And in the Grant settings, check “Require multifactor authentication“.
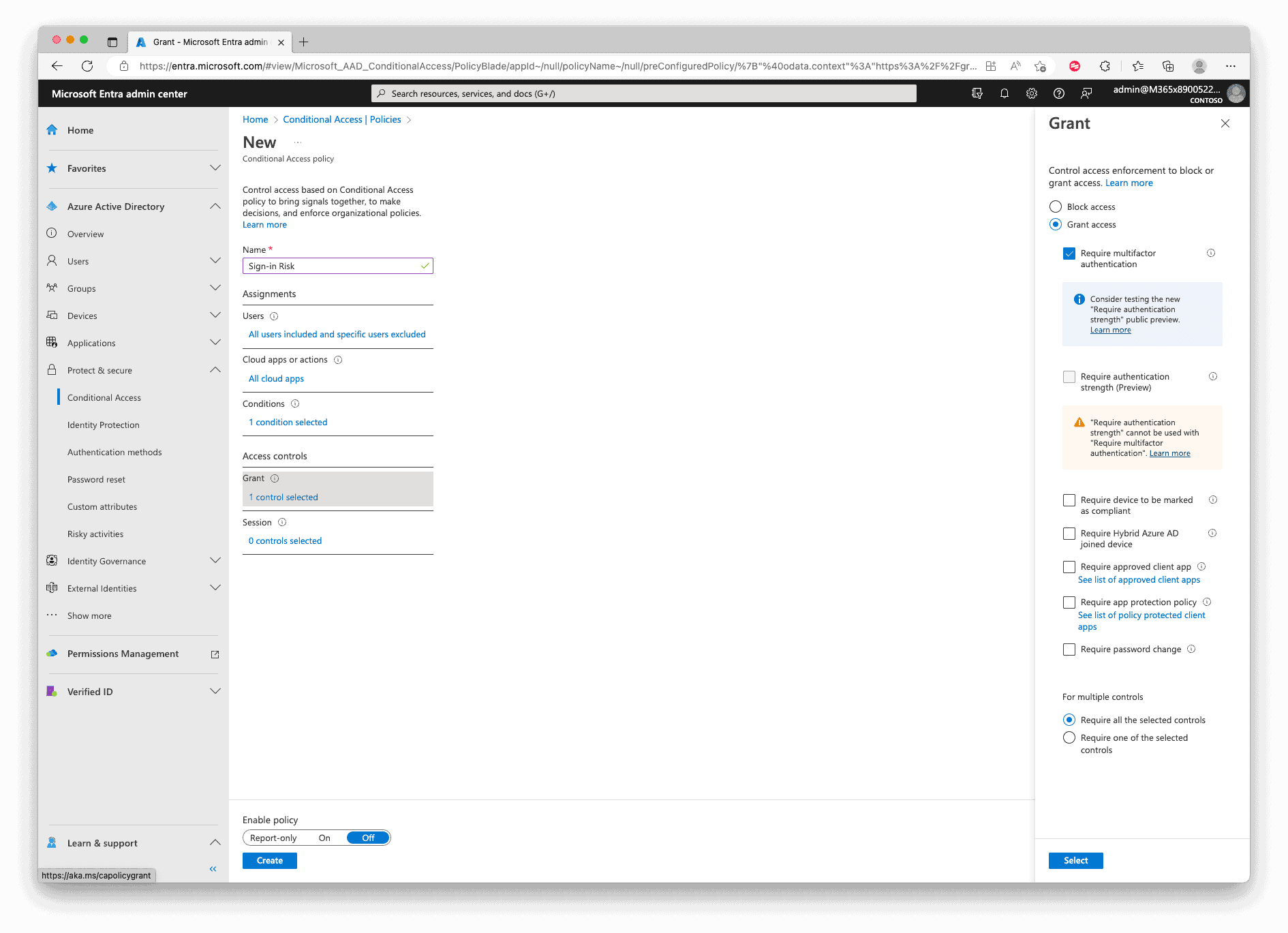
The Outcome of our policies will be when a risky sign-in is detected, the user needs to use multifactor authentication. When a risky user is detected, the user needs also to use multifactor authentication and further reset their password.
Monitor risky activities and export data
Via the menu item “Risky activities” and in the sub-category “Reports” you can monitor the risky activities like sign-ins and users, remediate problems manually, and also export risky sign-in data to Microsoft Sentinel, ELK, Splunk, and so on for a bigger picture. In my example, I logged in via different countries (via VPN) into my demo account of Nestor Wilke. By using the MFA during the login I remediated the risk.

Conclusion
Microsoft Azure Identity Protection is a simple yet powerful service that can help to protect your organization against identity-based attacks by detecting and auto-remediating potential risks associated with user accounts and sign-in attempts. With the use of machine learning and analytics, Azure Identity Protection provides administrators with insights into potential threats.
Resources
https://learn.microsoft.com/en-us/azure/active-directory/identity-protection/

